Building an Enterprise Root Certification Authority in Small and Medium Businesses
Introduction
Unprotected information exchange across the Internet, extranets, intranets, and between applications presents potential security risks to any organization today. The challenges include preventing an unauthorized third party from eavesdropping on information traveling over the Internet, masquerading as an authorized person, or disrupting the ability of an organization to conduct business.
This step-by-step guide will help you set up a public key certification authority (CA) in a network with servers running Linux or Microsoft etc, operating systems.
A CA is a service that issues and manages electronic credentials or certificates in a public key infrastructure (PKI). PKI is a system of digital certificates, CAs, and other registration authorities (RAs) that verify and authenticate the validity of each party that is involved in an electronic transaction through the use of public key cryptography. Standards for PKIs are still evolving, even as they are being widely implemented as a necessary element of electronic commerce. Many government agencies and private organizations have promulgated their own PKI standards. Consult with your legal counsel prior to implementing a PKI architecture to ensure compliance with all relevant local, state, federal, and international laws and regulations. To help to secure network communications between an organization and its employees, partners, vendors, and customers. A server running Windows Server 2003 Certificate Services can issue public key certificates to a person, device, or service. The certificate holder enabled applications and technologies to enable centrally managed strong authentication, to ensure data confidentiality, and to secure data exchange and the technologies providing a foundation for the following technologies and their associated business benefits:
Digital signatures. Establish non-repudiation, which is the ability to guarantee the authenticity of the sender.
Smart card usage. Provides two-factor authentication for smart card logon. Two-factor authentication requires a user to present a physical object (the smart card, which contains a chip that stores a digital certificate and the user's private key) plus a password or PIN in order to access network resources.
Secure e-mail. Services such as Secure/Multipurpose Internet Mail Extensions (S/MIME) provide confidential communication, data integrity, and non-repudiation for e-mails.
Software code signing. Authenticode technology allows software publishers to digitally sign any form of active content, including multiple-file archives. These signatures can be used to verify both the identity of the content publisher and the integrity of the content at the time of download.
Internet Protocol Security (IPSec). A suite of protocols that allows encrypted and digitally signed communication between two computers or between a computer and a router over a public network.
Encrypting file system. Supports encryption and decryption of files and folders.
Secure Web Connections using Secure Sockets Layer (SSL) or Transport Layer Security (TLS). These protocols provide server and client authentication through a secured communications channel over public networks such as the Internet. Wireless versions of these protocols such as Wireless Transport Layer Security (WTLS) can be used to enhance the security of wireless networks.
The instructions provided in this document show you how to build an enterprise root CA, use a certificate template to enable client autoenrollment, and establish autoenrollment for wireless users. Specifically, you will learn how to perform the following tasks:
Install and configure an enterprise root CA.
Verify CA installation.
Install certificate templates.
Create a custom certificate template.
Configure a certificate template for client autoenrollment.
Grant enroll permissions for a default certificate template.
Configure the CA to issue certificates based on the certificate template.
Establish autoenrollment for wireless users.
After you complete these steps, your network will include an enterprise root CA and you will have access to all of the certificate templates available by using the Certificate Templates snap-in. In addition, client autoenrollment will strengthen authentication for your wireless users by requiring them to use digital certificates during the authentication process. Autoenrollment can make this requirement virtually transparent to users by enabling them to automatically request certificates, retrieve issued certificates, and renew expiring certificates. You can also broaden the protection the Linux OS provides to your network by expanding your use of the support additional applications such as digital signatures, IPSec, and so on, that were mentioned earlier.
Installing and Configuring an Enterprise Root Certification Authority
The installation process for a Certificate Services root authority generates a root CA certificate containing the CA's public key and the digital signature created by using the root's private key. This section provides the following step-by-step instructions for building an enterprise root CA, using a certificate template to enable client autoenrollment, and establishing autoenrollment.
To Install and configure an enterprise root CA.
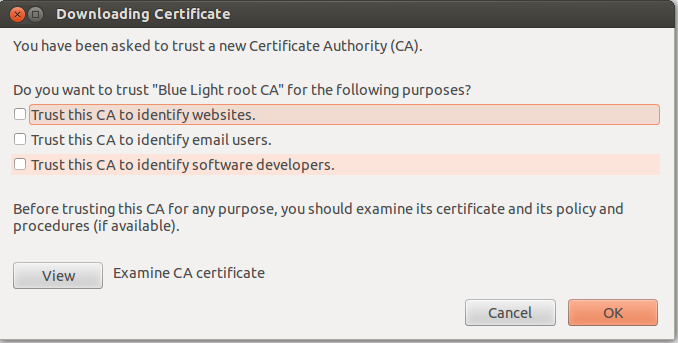
For Firefox Web Browser, by typing URL http://bluelightav.org/blca.crt , then ticking the empty boxes when this thing and press OK.
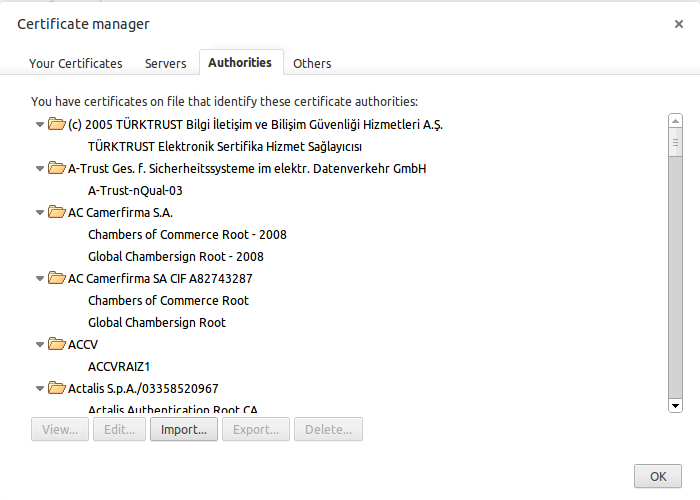
- For Google Chrome, typing the URL https://bluelightav.org/blca.crt it will download automatically. After by the google chrome homepage then chrome://chrome/settings/certificates then clicking the import button for certificate to download from the folder to certificate manger.
Verifying CA Installation
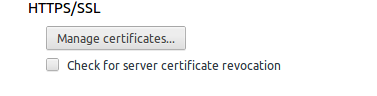
- The simplest way to verify the successful completion of the Certificate Services installation by back to chrome://chrome/settings/certificates by clicking the manage certificates
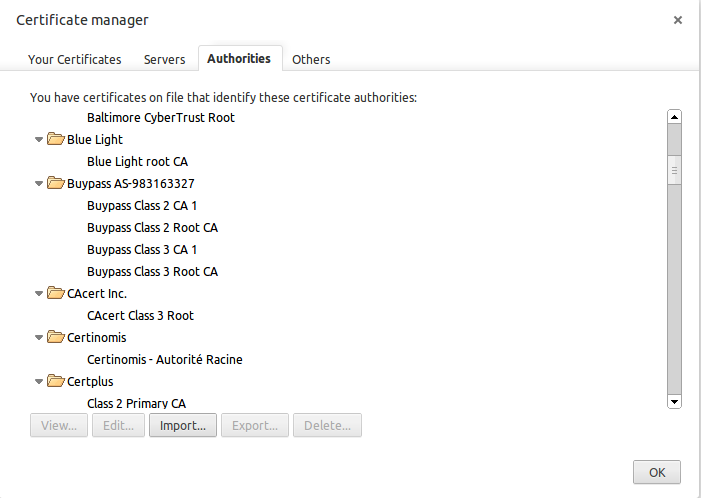
- And then the picture below shows the certificate manager will appear with Blue Light root CA has installed.
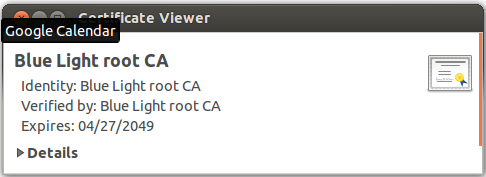
- Or by typing the URL http://bluelight.org/blca.crt after loading blca.crt folder then clicking on it will show this certificate viewer the picture below. That also Means installed.